Obtaining a Multi-Level Wildcard Let's Encrypt Certificate and Storing it in AWS Secrets Manager

In this tutorial, we will walk you through the process of obtaining a multi-level wildcard Let's Encrypt certificate and storing it in AWS Secrets Manager.
We'll also use Ansible to deploy an Nginx web server and retrieve the SSL/TLS keys from Secrets Manager to secure the web server.
Step 1: Obtain a Multi-Level Wildcard Let's Encrypt Certificate
We'll use Certbot to obtain a multi-level wildcard certificate for your domain. Certbot's DNS challenge method is suitable for wildcard certificates.
sudo certbot certonly --manual --preferred-challenges dns -d "*.yourdomain.com" -d "yourdomain.com"
Follow the prompts to complete the DNS challenge verification. Certbot will provide you with the certificate and key files.
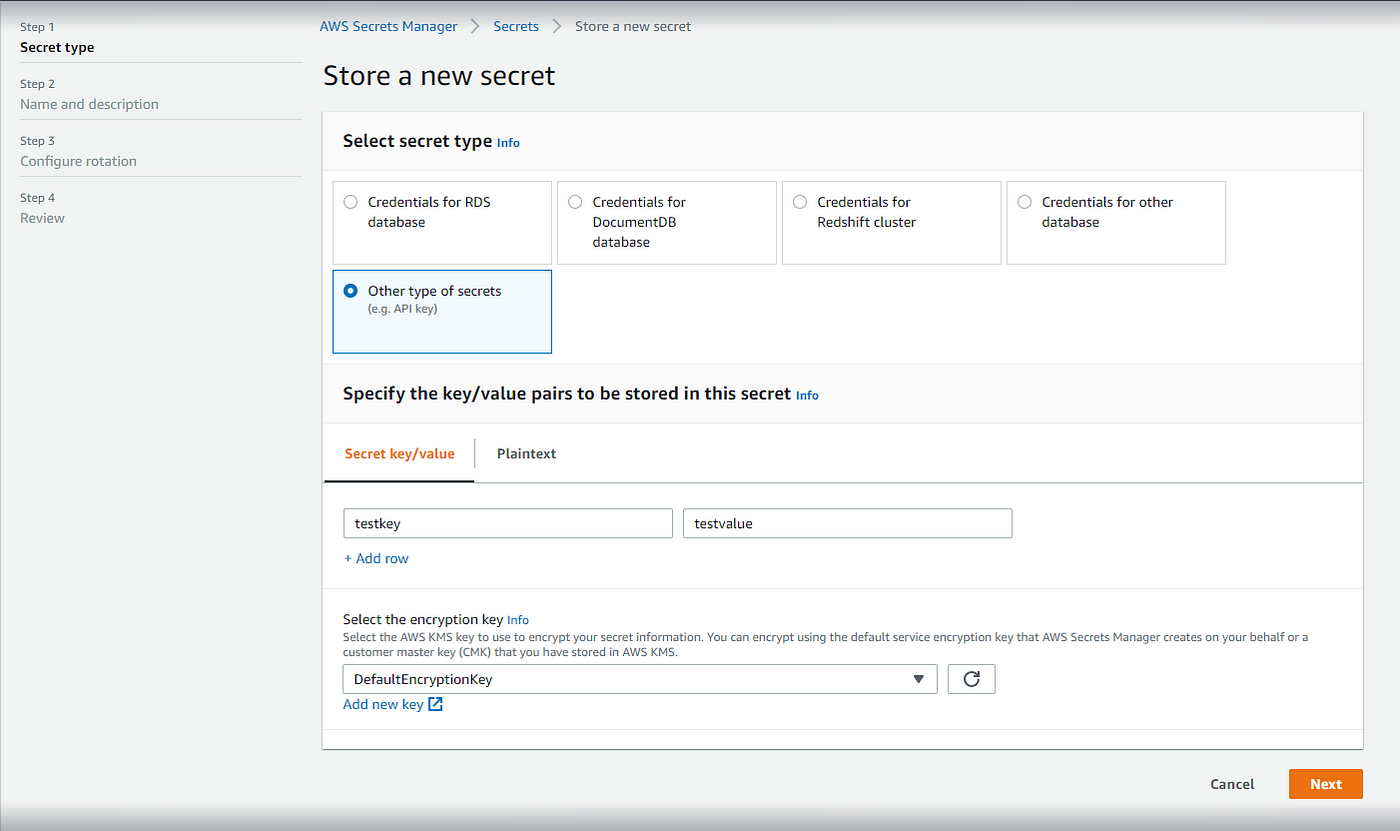
Step 2: Store the Certificate and Key in AWS Secrets Manager
- Log in to the AWS Management Console.
- Open the AWS Secrets Manager service.
- Click on "Store a new secret."
- Choose "Other type of secrets."
- For "Key/value pairs," provide the following:
- Key:
certificate - Value: The content of the
fullchain.pemfile generated by Certbot. - Key:
private_key - Value: The content of the
privkey.pemfile generated by Certbot.
- Key:
- Click "Next" and give your secret a name and description.
- Configure the rotation policy as per your organization's security policy or leave it disabled for manual rotation.
- Review and store the secret.
Step 3: Deploy Nginx using Ansible
Assuming you have Ansible configured for your environment, create an Ansible playbook to deploy Nginx and retrieve the SSL/TLS keys from AWS Secrets Manager.
---
- name: Deploy Nginx with SSL/TLS
hosts: your_webserver
become: yes
tasks:
- name: Install Nginx
apt:
name: nginx
state: present
notify:
- Start Nginx
- name: Copy SSL/TLS certificate and private key from AWS Secrets Manager
aws_secretsmanager_facts:
name: your-secrets-manager-secret-name
register: secrets_manager
- name: Create SSL/TLS certificate file
copy:
content: "{{ secrets_manager['SecretString'] | from_json | json_query('certificate') }}"
dest: /etc/ssl/certs/yourdomain.com.crt
notify:
- Restart Nginx
- name: Create SSL/TLS private key file
copy:
content: "{{ secrets_manager['SecretString'] | from_json | json_query('private_key') }}"
dest: /etc/ssl/private/yourdomain.com.key
notify:
- Restart Nginx
handlers:
- name: Start Nginx
service:
name: nginx
state: started
- name: Restart Nginx
service:
name: nginx
state: restarted
Make sure to replace your_webserver with the hostname of your server in the Ansible inventory file and your-secrets-manager-secret-name with the actual name of the secret stored in AWS Secrets Manager.
Step 4: Run the Ansible Playbook
Run the Ansible playbook to deploy Nginx and configure it with the SSL/TLS certificate and private key:
ansible-playbook nginx_deploy.yml
Nginx will be installed and configured with the SSL/TLS certificate and private key retrieved from AWS Secrets Manager.
Congratulations! You've obtained a multi-level wildcard Let's Encrypt certificate, stored it in AWS Secrets Manager, and deployed an Nginx web server secured with the SSL/TLS certificate using Ansible.


