AWS SSM with Ansible to Store Parameters and Secrets

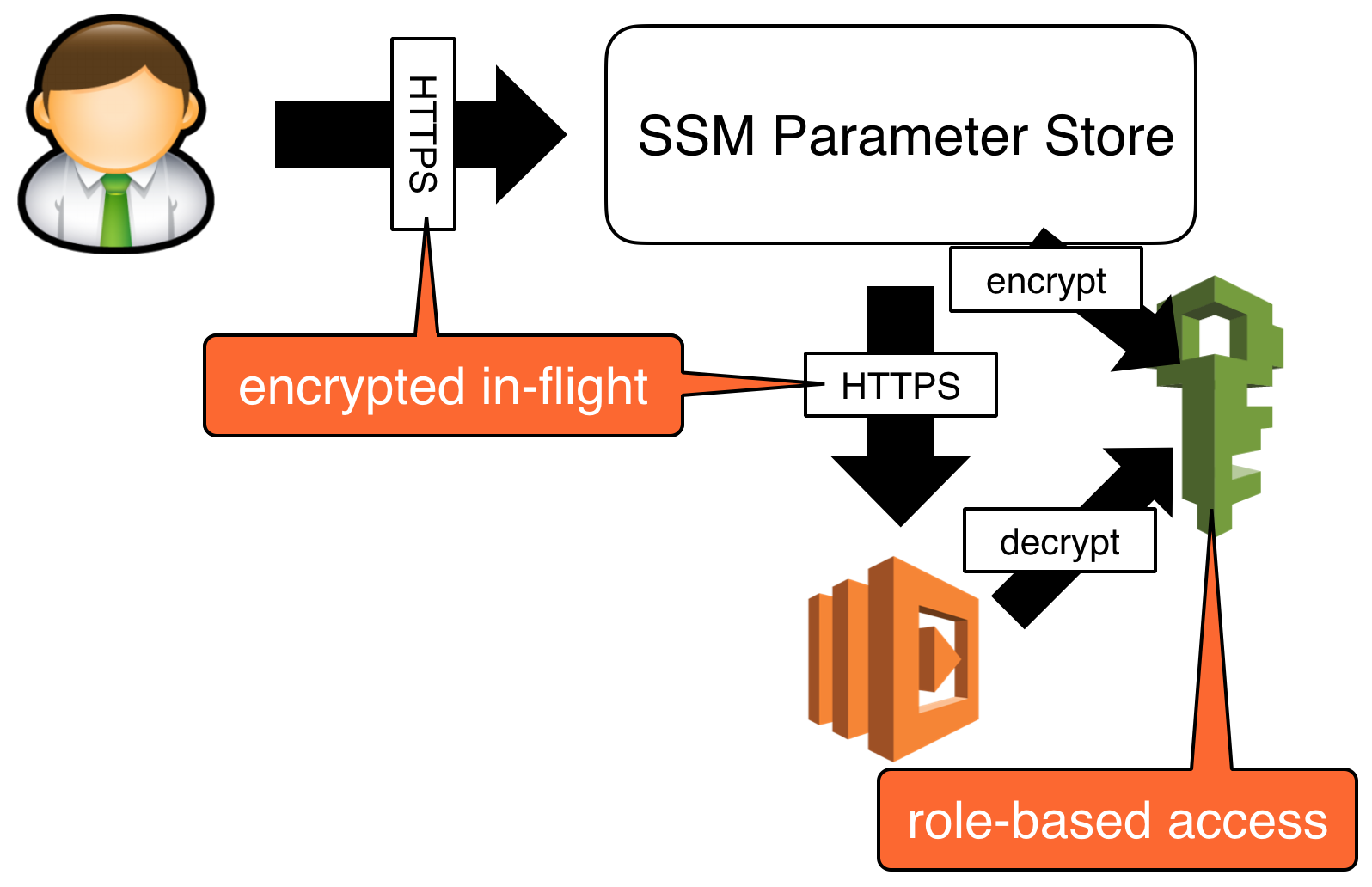
AWS Systems Manager Parameter Store (SSM Parameter Store) is a service that allows you to securely store configuration data, secrets, and other management information.
Integrating SSM Parameter Store with Ansible, a powerful automation tool, enables you to centralize and secure the storage of parameters and secrets while making them accessible for automation tasks. In this tutorial, we will guide you through the process of using AWS SSM with Ansible to store parameters and secrets.
Prerequisites
Before you begin, ensure you have the following prerequisites in place:
- AWS Account: You need an active AWS account with appropriate IAM permissions to access SSM Parameter Store.
- AWS CLI: The AWS Command Line Interface (CLI) should be installed and configured with the necessary credentials.
- Ansible Installed: Ansible should be installed on your local machine or control node. You can follow the official Ansible installation guide for your platform.
Step 1: Create SSM Parameters
You can create SSM parameters using the AWS Management Console, AWS CLI, or SDKs. For this tutorial, we will use the AWS CLI.
Create a String Parameter :
aws ssm put-parameter --name "/myapp/database/password" --value "mysecretpassword" --type "String" --overwriteCreate a SecureString Parameter (for Secrets) :
aws ssm put-parameter --name "/myapp/api/secret_key" --value "supersecretkey" --type "SecureString" --overwriteEnsure that you replace the parameter names, values, and types with your actual configuration data and secrets.
Step 2: Configure Ansible to Use AWS
To use AWS SSM Parameter Store with Ansible, you need to configure Ansible to access AWS services. You can do this by setting AWS credentials in your environment or using a configuration file. Here, we'll use the configuration file method.
Create an AWS configuration file (e.g., ~/.aws/config) with your AWS credentials:
[default]
aws_access_key_id = YOUR_ACCESS_KEY
aws_secret_access_key = YOUR_SECRET_KEY
region = YOUR_AWS_REGIONReplace YOUR_ACCESS_KEY, YOUR_SECRET_KEY, and YOUR_AWS_REGION with your AWS access credentials and region.
Step 3: Create an Ansible Playbook
Create an Ansible playbook that fetches parameters from SSM Parameter Store. For example, you can create a playbook (ssm_parameters.yml) like this:
---
- hosts: localhost
gather_facts: no
tasks:
- name: Fetch SSM Parameter (String)
aws_ssm:
name: "/myapp/database/password"
register: db_password
- name: Fetch SSM Parameter (SecureString)
aws_ssm:
name: "/myapp/api/secret_key"
with_decryption: true
register: secret_key
- name: Debug Parameter Values
debug:
var: item.value
with_items:
- "{{ db_password }}"
- "{{ secret_key }}"This playbook fetches both String and SecureString parameters from SSM Parameter Store. The with_decryption: true option is used to decrypt SecureString parameters.
Step 4: Run the Ansible Playbook
Run the Ansible playbook to fetch the parameters from SSM Parameter Store:
ansible-playbook ssm_parameters.ymlAnsible will retrieve the parameter values and display them in the output.
Conclusion
You've successfully used AWS SSM with Ansible to store and retrieve parameters and secrets securely. This integration allows you to centralize your configuration data and secrets in SSM Parameter Store while leveraging Ansible for automation tasks.
You can further extend this setup to automate deployments, manage secrets rotation, and ensure secure and efficient infrastructure management.