Creating a Network in Nebula: A Real-World Scenario

Nebula is a scalable and secure framework for building distributed networks. In this article, we'll guide you through creating a network using Nebula, including setting up a Nebula relay, and demonstrate a real-case scenario between several Linux servers.
Prerequisites
Before you start, ensure you have the following:
- Linux Servers: At least three Linux servers with SSH access.
- Nebula: Download and install Nebula from the official GitHub repository.
Step 1: Install Nebula
First, download and install Nebula on each of your Linux servers.
wget https://github.com/slackhq/nebula/releases/download/v1.5.2/nebula-linux-amd64.tar.gz
tar -xvf nebula-linux-amd64.tar.gz
sudo mv nebula /usr/local/bin/Network Diagram
- Central Relay (host1): Location: New York. IP Address : 192.168.100.1 , Role: Acts as a relay
- Host2: Location: London , IP Address: 192.168.100.2 , Role: Connects to host1 through Nebula relay
- Host3: Location: Tokyo , IP Address: 192.168.100.3 , Role: Connects to host1 through Nebula relay
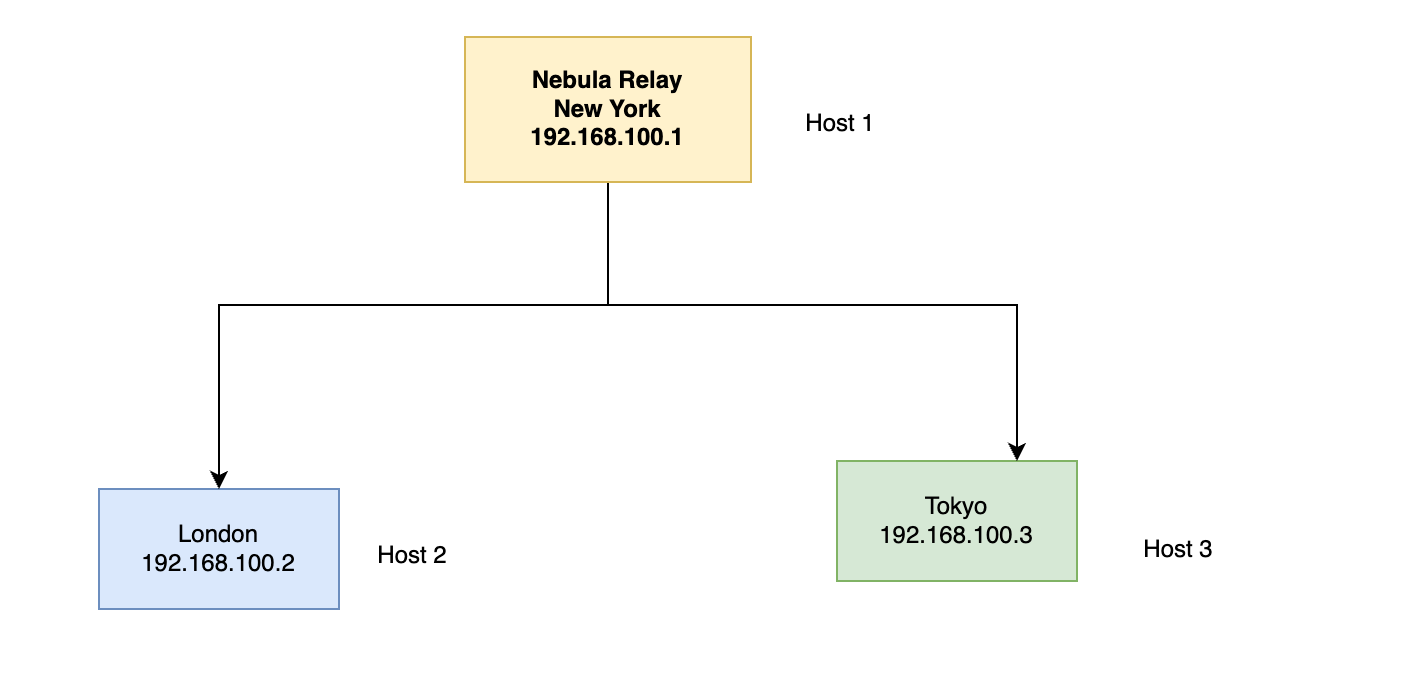
Connections:
- Relay Connections:
- An arrow from host2 (London) to host1 (New York)
- An arrow from host3 (Tokyo) to host1 (New York)
Nebula Relay:
- Label: "Nebula Relay"
- Position: Central label connected to host1
Here is a basic layout you can use to draw the diagram:
Step 2: Generate Nebula Certificates
Nebula requires certificates for secure communication between nodes. Generate these certificates on a central machine.
nebula-cert ca -name "My Nebula CA"
nebula-cert sign -name "host1" -ip "192.168.100.1/24"
nebula-cert sign -name "host2" -ip "192.168.100.2/24"
nebula-cert sign -name "host3" -ip "192.168.100.3/24"Distribute the certificates to the respective servers:
ca.crtto all servers.host1.crtandhost1.keytohost1.host2.crtandhost2.keytohost2.host3.crtandhost3.keytohost3.
Step 3: Configure Nebula
Create a configuration file for each server. Below is a sample configuration for host1.
pki:
ca: /etc/nebula/ca.crt
cert: /etc/nebula/host1.crt
key: /etc/nebula/host1.key
static_host_map:
"192.168.100.2": ["10.0.0.2:4242"]
"192.168.100.3": ["10.0.0.3:4242"]
lighthouse:
am_lighthouse: true
interval: 60
hosts:
- "192.168.100.2"
- "192.168.100.3"
listen:
host: 0.0.0.0
port: 4242
tun:
dev: nebula1
cidr: 192.168.100.1/24
firewall:
outbound:
- port: any
proto: any
host: any
Repeat for host2 and host3, adjusting the IP addresses accordingly.
Step 4: Start Nebula
Start the Nebula service on each server.
sudo nebula -config /etc/nebula/config.yml
Step 5: Setting Up Nebula Relay
Nebula relay helps to bridge networks that are not directly reachable. Assume host1 acts as the relay.
- Edit
host1configuration to enable relay.
relay:
enable: true
routes:
- dst: 192.168.100.2/24
- dst: 192.168.100.3/24
- Configure
host2andhost3to use the relay.
For host2 and host3, add the following in their configuration:
static_host_map:
"192.168.100.1": ["10.0.0.1:4242"]
"192.168.100.3": ["10.0.0.3:4242"]
lighthouse:
am_lighthouse: false
interval: 60
hosts:
- "192.168.100.1"
relay:
use_relay: ["192.168.100.1"]Real-Case Scenario
Imagine three servers located in different geographical regions:
host1in New York (Relay)host2in Londonhost3in Tokyo
These servers need to communicate securely and efficiently despite being behind different firewalls and NATs.
- Configuration: Follow the steps above to install and configure Nebula on each server.
- Relay Setup: Configure
host1as a relay to facilitate communication betweenhost2andhost3. - Communication: Test the setup by pinging between hosts.
# On host2
ping 192.168.100.3
# On host3
ping 192.168.100.2
Conclusion
By following these steps, you've set up a secure and efficient network using Nebula, complete with a relay to bridge otherwise unreachable networks.
Nebula's flexibility and security features make it an excellent choice for building distributed networks across different regions and environments.
For more information and advanced configurations, refer to the Nebula documentation.

